Facebook on Wednesday said it took steps to dismantle malicious activities perpetrated by two state-sponsored hacking groups operating out of Palestine that abused its platform to distribute malware.
The social media giant attributed the attacks to a network connected to the Preventive Security Service (PSS), the security apparatus of the State of Palestine, and another threat actor known as Arid Viper (aka Desert Falcon and APT-C-23), the latter of which is alleged to be connected to the cyber arm of Hamas.
Both the groups appear to have leveraged the platform as a springboard to launch a variety of social engineering attacks in an attempt to lure people into clicking on malicious links and installing malware on their devices. To disrupt the adversary operations, Facebook said it took down their accounts, blocked domains associated with their activity, and alerted users it suspects were singled out by these groups to help them secure their accounts.
Android Spyware in Benign-Looking Chat Apps
PSS is said to have used custom-built Android malware that was disguised as secure chat applications to stealthily capture device metadata, capture keystrokes, and upload the data to Firebase. In addition, the group deployed another Android malware called SpyNote that came with the ability to monitor calls and remotely access the compromised phones.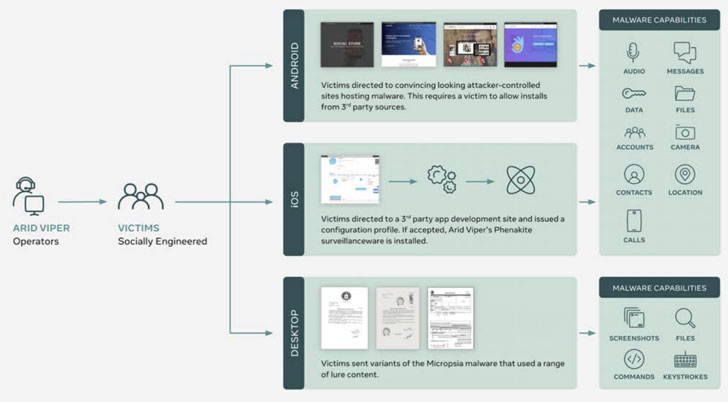
This group used fake and compromised accounts to create fictitious personas, often posing as young women, and also as supporters of Hamas, Fatah, various military groups, journalists, and activists with an aim to build relationships with the targets and guide them toward phishing pages and other malicious websites.
“This persistent threat actor focused on a wide range of targets, including journalists, people opposing the Fatah-led government, human rights activists and military groups including the Syrian opposition and Iraqi military,” Facebook researchers leading the cyber espionage investigations said.
A Sophisticated Espionage Campaign
“Lure content and known victims suggest the target demographic is individuals associated with pro-Fatah groups, Palestinian government organizations, military and security personnel, and student groups within Palestine,” the researchers added.
Facebook suspects Arid Viper used the iOS malware only in a handful of cases, suggesting a highly-targeted operation, with the Hamas-linked hackers simultaneously focusing on an evolving set of Android-based spyware apps that claimed to facilitate dating, networking, and regional banking in the Middle East, with the adversary masking the malware as fake app updates for legitimate apps like WhatsApp.
Once installed, the malware urged victims to disable Google Play Protect and give the app device admin permissions, using the entrenched access to record calls, capture photos, audio, video, or screenshots, intercept messages, track device location, retrieve contacts, call logs, and calendar details, and even notification information from messaging apps such as WhatsApp, Instagram, Imo, Viber, and Skype.
In an attempt to add an extra layer of obfuscation, the malware was then found to contact a number of attacker-controlled sites, which in turn provided the implant with the C2 server for data exfiltration.
“Arid Viper recently expanded their offensive toolkit to include iOS malware that we believe is being deployed in targeted attacks against pro-Fatah groups and individuals,” Facebook researchers said. “As the technological sophistication of Arid Viper can be considered to be low to medium, this expansion in capability should signal to defenders that other low-tier adversaries may already possess, or can quickly develop, similar tooling.”
THE HACKER NEWS






